8 minutes
Encrypting the Home Partition on an Existing Linux Installation
The Need for Encryption
Think of all the private data that people typically store on their computer: family pictures and videos, financial documents such as tax returns and bank statements, passwords (seriously ?!), and even source codes, all of which would have severe repercusions if a third-party gains access to them.
Unauthorized access and theft of personal data are responsible for several ramifications like identity theft, fake profiles, intellectual property theft, and credit card fraud, among others every year. According to the “Consumer Sentinel Network Data Book” by the Federal Trade Commission, government-issued documents are most targeted by hackers to perpetuate identity theft.
All these issues stem from either poorly secured storage devices or malware. Unfortunately, while many of us are careful while installing new software, sharing external drives or pendrives, and browing the web vigilantly to avoid malware, we often tend to neglect that
Info
an unencrypted disk makes our personal data vulnerable even if the computer is not infected with malware.
The Operating System password becomes entirely useless if the boot process is bypassed and the storage device is accessed directly. Even if your computer or hard disk has not been stolen, nothing prevents someone from plugging a bootable USB drive into your computer, boot from it, and view all your data in plaintext. Hence, a login password or PIN is simply not sufficient to protect your personal information.
Not using encryption in 2022 is the equivalent of walking around wearing a very lose pair of jeans without belts on. Every step you take brings the jeans closer to falling off! Even if you’re adamant and think that you’re going to pull up your jeans every once in a while to avoid such a situation, Murphy’s Law tells us that
Quote
Anything that can go wrong will go wrong [sooner or later].
This means as time passes, the possibility that you become a victim of cybercrime always increases, no matter how unlikely that event appears to you. Therefore, the best time to take action is now.
Fortunately, many Linux distros provide an option to encrypt the home partition during the installation process. But what if you didn’t select that option during installation, and now you want to keep your data safe from prying eyes? In this blog post, we’re going to see how to encrypt the home partition without reinstalling Linux.
Step 1: Backup
Safety is not negotiable and backups are a very important cornerstone of safety when it comes to data. This is why it is imperative to backup your files before the encryption process. Storing backups on a disk that’s permanently connected to your computer will only lead to regrets later on!
Tip
The best storage medium to store your backups is an external disk or in the cloud (assuming the latter uses end-to-end encryption and you have 2FA enabled).
The /home directory is where all users’ personal files and directories (Desktop, Documents, Downloads, Music, Pictures, Videos, etc) are stored on Unix-like operating systems. Therefore, it makes sense to backup the entirety of /home. This can easily be achieved using rsync <source> <destination>.
The following commands will copy all files and directories (including hidden files) located in /home to the specified destination.
sudo rsync -avP /home/* /dev/sdxx/backup_dir
sudo rsync -avP /home/.[^.]* /dev/sdxx/backup_dir
Note
/dev/sdxx/backup_dir with the absolute path of your backup destination!You now have a complete backup of the /home directory.
Step 2: Create a Separate Partition for /home
Run the following command to quickly identify the configuration of your Linux installation:
lsblk | grep "/home"
If the above command displays some text containing /home, it means the root directory / and home directory /home are already on different partitions. If that’s the case, you should skip Step 2 and go directly to Step 3.
On the other hand, if the above command displays an empty output, it means both the root directory / and home directory /home are located on the same partition. Therefore, a new partition will have to be created specifically for /home.
Danger
Assuming that you have already backed up your /home directory as explained in Step 1, you can now delete your files in /home to make space for the new partition. We’ll restore the backup later after creating the encrypted partition. Run the following command to free up space:
sudo find /home -type f -o -type d -exec rm -rf "{}" \;
Next, we need to shrink the current Linux partition. Begin by launching gparted with elevated privileges:
sudo gparted
In gparted, right click on the partition whose mount point is
/and select Resize / Move.Enter anything between 30 GB to 40 GB as new space (MiB).
Tip
You will have to convert GB (Gigabyte) into MiB (Mebibyte):
1 GB = 953.6743 MiBClick on Resize. This will shrink your root partition to the size you entered above.
We’ll now use the resulting free space to allocate a new partition for
/home. Right click on the unallocated space in gparted and select New.Set “File System” to ext4 and “Create as” to Primary Partition. Then click on Add.
Step 3: Encrypt to Your Heart’s Content
We will make use of a utility called cryptsetup to encrypt the home partition. If you don’t have it installed already, you can do so using your package manager.
Now, run the following command in your Terminal:
sudo fdisk --list | grep -E "/dev/sd|/dev/nvme"
This will list information about all partitions. Identify the partition that you would like to use as /home and note the partition name (not the disk name!) found in the first column of the output and having the following format: /dev/xxxx.
Once you are certain about which partition to use as /home, we can now encrypt it.
- First, let’s create a shell variable to denote the
homepartition.
export NEW_HOME_PARTITION="/dev/xxxx"
Note
/dev/xxxx with the correct partition name you identified above!- Then, unmount the new partition that will be encrypted. If you get any error, simply ignore it.
sudo umount $NEW_HOME_PARTITION
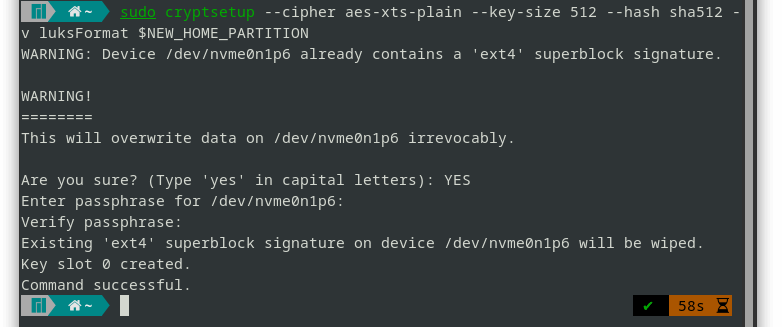
- Format the new partition as a LUKS device (essentially encrypting it):
sudo cryptsetup --cipher aes-xts-plain64 --key-size 512 --hash sha512 -v luksFormat $NEW_HOME_PARTITION
You will be asked to enter a passphrase for the encrypted partition. Enter a strong password (at least 12 characters) containing a mix of lowercase and uppercase letters, numbers, and symbols.
- Unmount the encrypted partition. If you get any error, simply ignore it.
sudo umount $NEW_HOME_PARTITION
- Open the new encrypted LUKS partition with mapping name
crypthome
sudo cryptsetup -v luksOpen $NEW_HOME_PARTITION crypthome
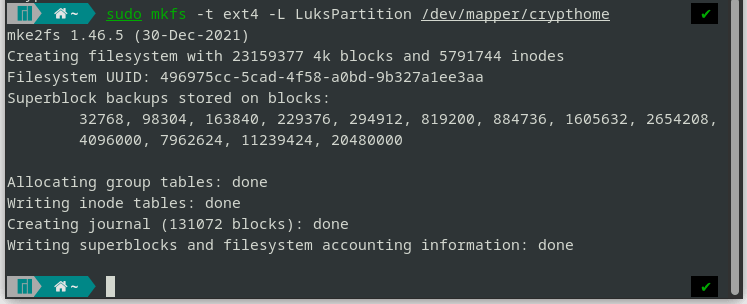
- Create
ext4filesystem on the encrypted partition.
sudo mkfs -t ext4 -L LuksPartition /dev/mapper/crypthome
- Check if the
ext4filesystem has been created properly on the encrypted partition.
sudo lsblk -f /dev/mapper/crypthome
- Copy the
UUIDof the encrypted partition.
sudo cryptsetup luksUUID $NEW_HOME_PARTITION
- Now, let’s create another shell variable to denote the
UUIDof the encrypted partition.
export NEW_PARTITION_UUID="c3a2f289-XXXX-4c4a-XXXX-bc3e726a3377"
Careful
NEW_PARTITION_UUID shell variable in the above command with the correct UUID that you copied in step 8.
echo $NEW_PARTITION_UUID
- Add entry in
/etc/crypttab
echo "luks-$NEW_PARTITION_UUID UUID=$NEW_PARTITION_UUID none luks" | sudo tee -a /etc/crypttab
- Add entry in
/etc/fstab
echo "/dev/mapper/luks-$NEW_PARTITION_UUID /home ext4 defaults,relatime 0 2" | sudo tee -a /etc/fstab
- Mount the encrypted partition at
/mnt/crypthome
sudo mkdir -p /mnt/crypthome/
sudo mount /dev/mapper/crypthome /mnt/crypthome
- Now we can restore the backup of the
/homedirectory onto the encrypted partition.
Note
/dev/sdxx/backup_dir in the commands below with the actual absolute path of your backup source!sudo rsync -avP /dev/sdxx/backup_dir /mnt/crypthome
sudo rsync -avP /dev/sdxx/backup_dir/.[^.]* /mnt/crypthome
- Delete the current
/home. Then, unmount the encrypted partition and mount it at/home:
sudo rm -rf /home/*
sudo umount /mnt/crypthome
sudo mount /dev/mapper/crypthome /home
- One last important thing is to backup the LUKS header of the encrypted partition.
sudo cryptsetup -v luksHeaderBackup $NEW_HOME_PARTITION --header-backup-file LuksHeaderBackup.bin
Tip
LuksHeaderBackup.bin on an external disk. If the header of the encryted partition gets corrupted someday and you are unable to log in, you can easily boot from a Linux live USB and restore the LUKS header as follows:
sudo cryptsetup -v luksHeaderRestore $NEW_HOME_PARTITION --header-backup-file LuksHeaderBackup.bin
The next time you turn on your computer, you should see a new interface prompting you to enter a password to unlock the encrypted disk.

The usual login screen will appear only if the correct decryption password is provided. From now on, even if your hard disk or device is stolen, your files will be unreadable to any third-party.
And voila! The content of your home partition is now reserved for your eyes only :P
If you’re looking to secure your Linux installation even further, please check how to use an encrypted swap partition .
# Footnotes
https://infosecwriteups.com/how-luks-works-with-full-disk-encryption-in-linux-6452ad1a42e8
https://blog.tinned-software.net/create-a-luks-encrypted-partition-on-linux-mint/
https://www.tecmint.com/move-home-directory-to-new-partition-disk-in-linux/
https://www.cyberciti.biz/faq/linux-unix-appleosx-bsd-rsync-copy-hidden-dot-files/
https://gitlab.com/cryptsetup/cryptsetup/-/wikis/FrequentlyAskedQuestions#10-luks2-questions


Comments
GUESTADMINGUESTGUESTADMINGUESTADMINGUESTADMINADMINGUESTPlease wait...