6 minutes
How to Use an Encrypted Swap Partition with Support for Hibernation on Linux
Why Encrypt the Swap Partition?
Encrypting the home partition
is a good first step toward ensuring data confidentiality. However, a typical system usually stores some information outside /home such as in swap partitions which are not encrypted by default. This poses a security threat as sensitive information can be gleaned from the swap partition, even if the /home partition is encrypted.
A potential remedy is to disable swap, but this solution is not the best as sometimes one would want to use a swap partition to support certain features such as hibernation. In this case, it is imperative to encrypt the swap partition as well. Having an encrypted swap partition ensures that data cannot be leaked from the swap space.
In this article, we’re going to see how to enable encryption on the swap partition, all while having suspend-to-disk support. When the computer is turned on from a previous hibernation, the encrypted swap partition is unlocked, and the system resumes from there.
Step 1: Disable Current Swap
First, it is important to determine whether your system is already using swap space.
If that’s the case, then you should disable it as follows:
Moreover, any line in the /etc/fstab file which references swap partitions should be removed.
Step 2: Choose a Swap Partition
Next, run this command in the Terminal to list all available partitions:
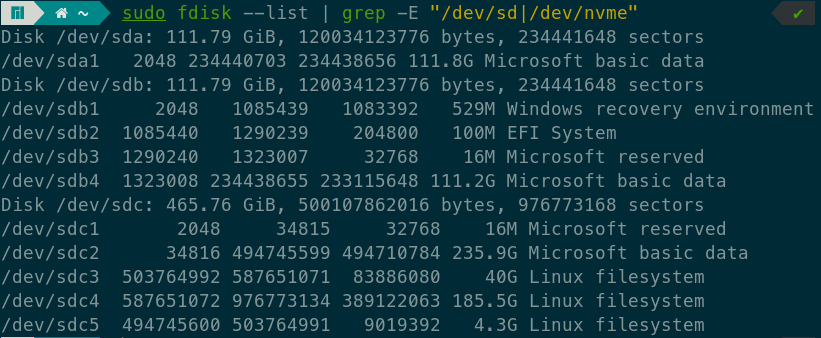
Choose the partition that you would like to use as swap and note the partition name (not the disk name!) found in the first column of the output and having the following format: /dev/xxxx.
If you do not have any free partition to use for the swap, you can shrink any partition of your choice to make space for a new partition using a utility such as gparted.
When allocating space for a swap partition, make sure the partition size is at least the square root of the total RAM size, rounded up to the nearest GB.
For example, if you have 8 GB RAM, sqrt(8) = 2.8284. This means the swap partition should be at least 3 GB, assuming you won’t be hibernating the system. For hibernation, you should factor in a couple more Gigabytes.
Step 3: Encrypt the Swap Partition Using LUKS
We will now encrypt the partition which will be used as swap. If you don’t have cryptsetup installed already, you can install it using your package manager.
- To make our task easier, let’s create a shell variable to denote the
swappartition.
Note
/dev/xxxx with the correct partition name from Step 2!- Then, unmount the new partition that will be encrypted. If you get any error, simply ignore it.
- Encrypt the partition by formatting it as a LUKS device:
You will be asked to enter a passphrase to encrypt the partition. Enter a strong password (at least 12 characters) containing a mix of lowercase and uppercase letters, numbers, and symbols.
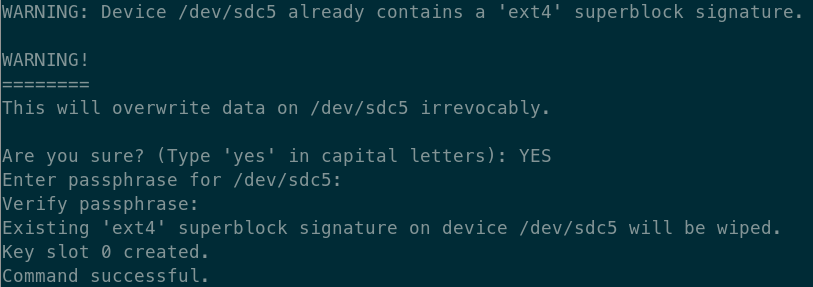
- Unmount the encrypted partition. If you get any error, simply ignore it.
Step 4: Create Swap Filesystem on the Encrypted Partition
Open the new encrypted LUKS partition with mapping name cryptswap.
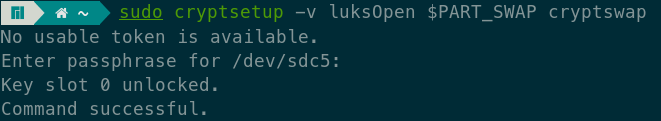
Then, create a swap filesystem inside the encrypted partition.
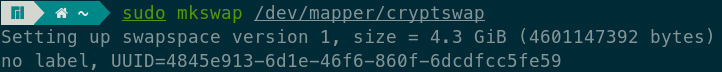
Step 5: Activate the Encrypted Swap Partition
It is a good idea to check if the swap partition was properly encrypted first:
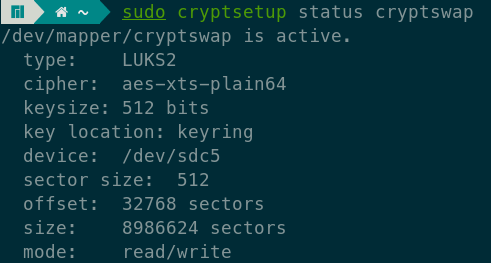
We can now activate the swap partition if the previous command gave a healthy output.
Step 6: Update System Configurations
At this point, the system should be using an encrypted swap partition. However, we need to change some configurations for three reasons:
- To unlock encrypted partitions at boot time.
- To instruct the kernel which partition to resume from, in case the system was hibernated during the previous shutdown.
- To persist using the encrypted swap partition between reboots.
Step 6.1: Unlock Encrypted Partitions at Boot Time
Let’s create another shell variable to denote the luksUUID of the encrypted swap partition.
Careful
UUID_SWAP shell variable has been set correctly.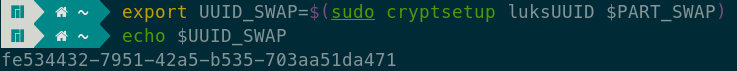
Step 6.1.1: For Manjaro, Arch Linux, and Derivatives
Note
We should configure mkinitcpio hooks so that the OS can access encrypted partitions before the login screen appears.
Comment the line starting with HOOKS= and use the one provided below instead:
Note
block and sd-encrypt hooks to be in that order, and before the filesystems hook.Then, rebuild all initramfs as follows:
Step 6.1.2: For Ubuntu, Debian, and Derivatives
Note
Add entry in /etc/crypttab
Step 6.2: Resuming From Hibernation Using the Swap Partition
Step 6.2.1: For Manjaro, Arch Linux, and Derivatives
Note
It is possible to instruct the kernel which encrypted partition to unlock and resume from through the rd.luks.name and resume directives respectively.
These should be added on the line starting with GRUB_CMDLINE_LINUX_DEFAULT (within the double quotes) in the /etc/default/grub file.
It is possible to achieve this automatically by issuing this sed command:
Because we had a shell variable $UUID_SWAP earlier, it will be expanded automatically, and this is what sed added in my case:
For example, on my setup the complete modified line in the /etc/default/grub file looks like this:
Then, run these commands for GRUB to use the updated configuration:
Step 6.2.2: For Ubuntu, Debian, and Derivatives
Note
Edit the /etc/initramfs-tools/conf.d/resume file. Replace the existing RESUME line with the following line:
If the file does not exist, create it with only that line.
Important
Rebuild all initramfs:
Step 6.3: Persist the Encrypted Swap Partition Between Reboots
Add entry in /etc/fstab by running this command:
Note
poweroff
Afterwards, you can hibernate the system through the GUI or by running this command in the Terminal:
You can still also do a normal shutdown if you don’t want to hibernate every time.
Conclusion
From now on, you should see a prompt to enter a passphrase for unlocking the swap partition whenever the computer is turned on. If you have other encrypted partitions (e.g /home) with the same password, you will be asked to enter the password only once per boot.
Congrats for adding “resume from hibernation” feature on an encrypted swap partition, and more importantly, for making your Linux installation more secure!
# Footnotes
https://wiki.archlinux.org/title/Data-at-rest_encryption
https://wiki.archlinux.org/title/Dm-crypt/Encrypting_an_entire_system#LUKS_on_a_partition
https://wiki.archlinux.org/title/Swap
https://www.man7.org/linux/man-pages/man5/fstab.5.html
https://forum.manjaro.org/t/how-to-rebuild-initramfs/65945/3
https://wiki.archlinux.org/title/Dm-crypt/System_configuration#crypttab
https://wiki.archlinux.org/title/Dm-crypt/Swap_encryption
https://wiki.archlinux.org/title/Power_management
https://help.ubuntu.com/community/EnableHibernateWithEncryptedSwap

Comments
GUESTGUESTGUESTPlease wait...